Configuring AP AAA Servers
To add and manage AAA servers that the controller can use to authenticate users, complete the following steps.
- Select Administration > Admins and Roles > AAA.
-
From
AP AAA Servers, click
Create.
The
Create Administrator AAA Server page is displayed.
Figure 214 Creating an Administrator AAA Server
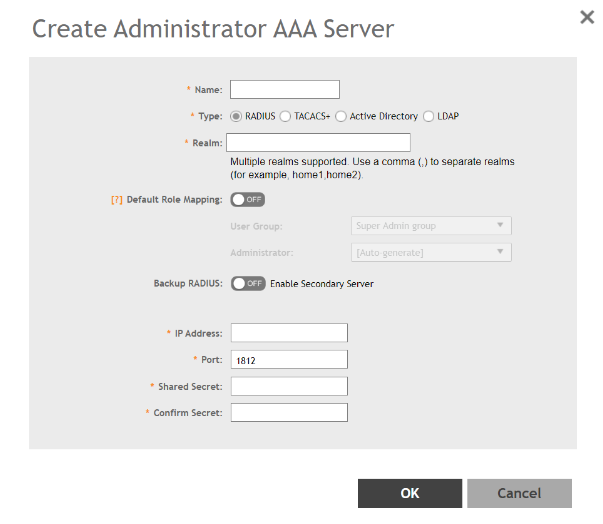
- Enter the AAA server name.
-
For
Type, select the type of AAA server to authenticate users:
- RADIUS
- TACACS+
- Active Directory
- LDAP
-
For
Realm, enter the realm or service.
Multiple realms or services are supported. Separate multiple realms or services with a comma.NOTEBecause the user login format (User Account + @ + Realm) includes a special character, the at symbol (@), the user account must not include the at symbol (@) separately on the AAA server.
-
Enable or disable
Default Role Mapping.
If enabled, AAA users are automatically mapped to a default local admin user or group permission even if the AAA server does not use mapping attributes.
If disabled, the AAA administrator must be mapped to a local SZ Admin user with matching AAA attributes for the RADIUS, TACACS+, Active Directory, or LDAP servers.
- On a RADIUS server, the user data can use the VSA Ruckus-WSG-User attribute with a value depending on the SZ users or permissions you want the RADIUS user to map.
- On a TACACS+ server, the user data can use the user-name attribute with the user1, user2, or user3 value depending on the SZ users or permissions you want the TACACS+ user to map.
- On an Active Directory or LDAP server, the user data can belong to the group cn=Ruckus=WSG-SZAdminName (for example, cn=Ruckus-WSG-user1, depending on the SZ users or permissions you want the Active Directory or LDAP user to map.
NOTEYou can use the mapping attributes on AAA and enable Default Role Mapping at the same time, but the mapping attributes override Default Role Mapping. - For Backup RADIUS, select Enable Secondary Server if a secondary RADIUS server exists on the network. Refer to step 9 for configuration settings.
-
Under
Primary Server, configure the settings of the primary AAA server.
- IP Address: Enter the IP address of the AAA server.
- Port: Enter the UDP port that the RADIUS server is using. The default port is 1812.
- Shared Secret: Enter the shared secret.
- Confirm Secret: Re-enter the shared secret to confirm.
- Windows Domain name: Enter the domain name for the Windows server.
- Base Domain Name: Enter the name of the base domain.
- Admin Domain Name: Enter the domain name for the administrator.
- Admin Password: Enter the administrator password.
- Confirm Password: Re-enter the password to confirm.
- Key Attribute: Enter the key attribute, such as UID.
- Search Filter: Enter a filter by which you want to search, such as objectClass=*.
-
Under
Secondary Server, configure the settings of the secondary RADIUS server.
- IP Address: Enter the IP address of the AAA server.
- Port: Enter the UDP port that the RADIUS server is using. The default port is 1812.
- Shared Secret: Enter the shared secret.
- Confirm Secret: Re-enter the shared secret to confirm.
-
Under
Failover Policy at NAS, configure the settings of the secondary RADIUS server.
- Request Timeout: Enter the timeout period in seconds. After the timeout period, an expected RADIUS response message is considered to have failed.
- Max Number of Retries: Enter the number of failed connection attempts. After the maximum number of attempts, the controller tries to connect to the backup RADIUS server.
- Click OK.
NOTE
You can also edit, clone, and delete the server by selecting the options
Configure,
Clone, and
Delete, respectively, from the
Administrator tab.
Parent topic: Working with AAA Servers
