Creating Account Security
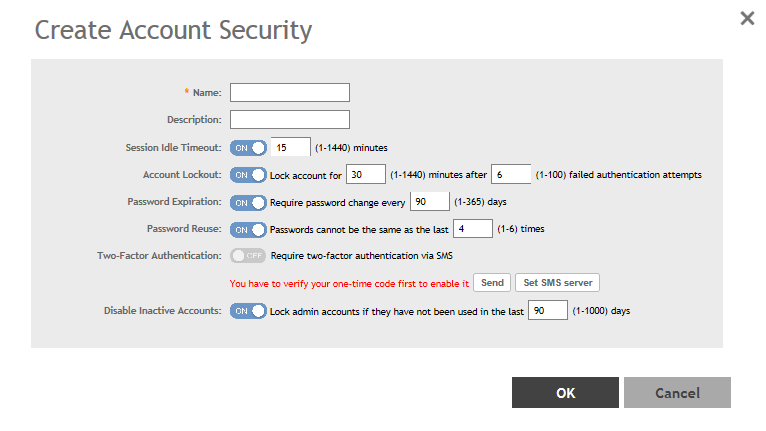
Creating an account security profile enables end-users to control administrative accounts to better manage admin accounts, passwords, login, and DoS prevention.
You have created the account security profile.
With new enhancements to account security, SmartZone has a complete feature set to make PCI compliance very simple and straightforward. In addition to local PCI enforcement settings, SmartZone also integrates with SCI for reporting and analytics. SCI version 5.0 and above supports a PCI compliance report, which is based on the relevant PCI-related configuration settings throughout SmartZone. To facilitate the SmartCell Insight PCI report, the SmartZone is capable of sending the following information to SCI:
- Configuration messages as separated GPB messages.
- WLAN configuration
- Default configuration changes
- Controller information which identifies the SZ model
- Encryption details of communication, for example: CLI, SSH, telnet, Web, API.
- Inactive user IDs and session timeout
- Authentication mechanism enforced on user IDs.
- Enforcement of password.
- Supported mechanism on SZ that can be provided to SCI.
- User IDs that are locked after failed attempts.
- Authentication credentials that are unreadable and encrypted during transmission.
- Enforcement of password standards.
- Disallowing duplicate password feature is enabled.
- If rogue AP detection is enabled on each AP.
To learn more about SCI and the PCI compliance report it provides, check the product page (https://www.ruckuswireless.com/products/smart-wireless-services/analytics) and documentation on Ruckus support (https://support.ruckuswireless.com.