Use case 1: 802.1X authentication with dynamic VLAN assignment
This use case shows the configuration required on a Brocade switch to authenticate an 802.1X client and assign the client to a VLAN dynamically. In the following example, after authentication, the PC will be placed in VLAN 200.
Figure 13
802.1X authentication with dynamic VLAN assignment
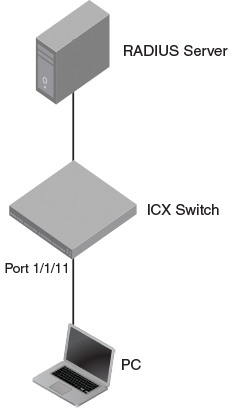
RADIUS configuration
Create a user profile on the RADIUS server and configure the attributes in the following table.
| Attribute | Value |
|---|---|
| Tunnel-Medium-Type | IEEE-802 |
| Tunnel-Pvt-Group-ID | 200 |
| Tunnel-Type | VLAN |
Brocade switch configuration
- Specify RADIUS as an authentication server. The following command configures the switch to use the configured RADIUS server to authenticate 802.1X authentication or MAC authentication clients.
device(config)# aaa authentication dot1x default radius
- Configure a RADIUS server. In the following example, the RADIUS server IP address is 10.20.64.208 and the shared key is "secret". The shared key should match the key given during client configuration on the RADIUS server. UDP port 1812 is used for RADIUS authentication messages and UDP port 1813 is used for RADIUS accounting messages.
device(config)# radius-server host 10.20.64.208 auth-port 1812 acct-port 1813 default key secret dot1x mac-auth web-auth
- Create a VLAN to be used as the auth-default VLAN. This VLAN must be configured to enable authentication. When any port is enabled for 802.1X authentication or MAC authentication, the port is moved into this VLAN by default as a MAC VLAN member. Sometimes the RADIUS server may authenticate the client but not return VLAN information on where the client should be placed. The auth-default VLAN is used in this scenario.
device(config)# vlan 2 name auth-default-vlan device(config-vlan-2)# exit
- Create a VLAN that will be used as a restricted VLAN. This VLAN must be active in the Brocade switch. A VLAN is active when it has at least one untagged or tagged member port. In the following example, VLAN 100 is made active by adding the unused port 2/1/13 as an untagged member.
device(config)# vlan 100 device(config-vlan-100)# untagged ethernet 2/1/13 device(config-vlan-100)# exit
- Create the VLANs that will be assigned to clients by RADIUS. RADIUS will return VLAN 200 for the PC. This VLAN must be active in the Brocade switch. A VLAN is active when it has at least one untagged or tagged member port. In this example, VLAN 200 is made active by adding the unused port 2/1/12 as an untagged member.
device(config)# vlan 200 device(config-vlan-200)# untagged ethernet 2/1/12 device(config-vlan-200)# exit
- Specify which VLAN ID to use as the auth-default VLAN under authentication mode. Refer to step 3 for the use of the auth-default VLAN.
device(config)# authentication device(config-authen)# auth-default-vlan 2
- To configure the authentication failure action as a restricted VLAN, specify a VLAN ID to be used as the restricted VLAN, and then configure the authentication failure action as the restricted VLAN. In this example, VLAN 100 is configured to be used as the restricted VLAN.
device(config-authen)# restricted-vlan 100 device(config-authen)# auth-fail-action restricted-vlan
- Enable 802.1X on the switch under authentication mode and enable 802.1X on port 1/1/11. Configure the port control mode as
auto in interface configuration mode. This mode enables 802.1X authentication on the interface.
device(config-authen)# dot1x enable device(config-authen)# dot1x enable ethernet 1/1/11 device(config-authen)# exit device(config)# interface ethernet 1/1/11 device(config-if-e1000-1/1/11)# dot1x port-control auto device(config-if-e1000-1/1/11)# exit
- To verify the authentication-related configuration on the switch, use the
show run authentication command. Authentication-related configurations are stored under the keyword "authentication".
device# show run authentication authentication critical-vlan 601 auth-default-vlan 2 restricted-vlan 100 auth-fail-action restricted-vlan re-authentication dot1x enable dot1x enable ethe 1/1/11 !
